Crowdstrike

This article is not financial advice, and the only reason I am writing it is so I can re-read my reasoning. I am posting it online so if I am wrong, others can correct my reasoning. Per Lynch:
Know what you own, and know why you own it
Do your own research 😊
Hey friends 👋
It was lovely meeting some of you at the Freetrade community event! This post will be about Crowdstrike. Hope you enjoy!
🤔 What is Crowdstrike?
Crowdstrike is an enterprise level security system, in their own words:
We stop breaches with our cloud-native endpoint security platform so our customers can go & change the world.
Specifically what they aim to achieve is:
- Virus detection.
- Detecting hackers / systems doing unusual things which are malicious.
- Provide an organisational overview of the movements of all machines.
First, we need some anti-virus history.
✍️ Signature based
McAffe was the first anti virus released, it was signature based which meant it looked for “strings” in previously known viruses. So as an example, the below code may be considered malicious:
DEL c://Which says “Delete everything under the C drive, which is the default Windows drive where all your files are stored”. McAffe would see this in a virus, create a “signature” for it and look for this signature in future viruses. So if a 2nd virus, which was designed to be smarter had that string it would be detected as a virus.
This only works if the viruses are very similar and have been seen before. For 0-days it’s impossible to detect, and McAffe had to regularly upload their entire signature database to the clients computers.
🕵️ Heuristic Analysis
Heuristics based anti-virus detection is the next level up. Instead of trying to find exact matches, it uses heuristics. Static Heuristic Analysis is where you decompile a program and if an arbitrary percentage of that file is copied from a virus, we can assume it is also a virus — just modified slightly.
Dynamic heuristics is similar to how scientists analyse a real world virus without endangering people. We find the virus, put it into a controlled & secure lab and conduct tests against it. Dynamic heuristics does this but in a virtual world.
This is the “current” geneartion of anti-virus software. But there are 2 problems:
- As more viruses come out, we add more viruses to our heuristics database. This grows in size and can mean users will have a database a couple of gigabytes large and will have to constantly download more samples.
- Sandboxing viruses is very expensive, and it will substantially slow down the users computer.
Is there a way we can do these things without affecting the users computer?
🛸 Extended Detection & Response (XDR)
Imagine instead of doing it all on the users computer, we just do it in the cloud. How will this work you might ask? Do we upload the users entire laptop the cloud? Not necessarily.
Crowdstrike has created a tiny little agent (it’s about 30mb) which places itself on the endpoint (a users machine in an organisation). This agent monitors the users laptop and streams data to Crowdstrike directly.

The agent can also detect viruses, it does this by looking at the behaviour of processes rather than signatures / heuristics of files. Primarily it watches running processes and using a machine learning model to detect anything suspicious.
It upgrades the machine learning model fairly frequently, but not as much as a typical anti virus product updates. The agent also uploads processes & data to the cloud so security operations analysts can look at this data, run models against it and determine if their organisation is has healthy security.
Because most of Crowdstrike is in the cloud (only the machine learning model is local, and that’s for break-glass emergencies) it is extremely lightweight and unnoticeable.
Calling it the “future of anti-virus” doesn’t do Crowdstrike justice. Where their business really lies is in the detection & response part. If you can’t stop an intruder the second they hack a machine, Crowdstrike will let you:
- Trace where the intruder came from and what they did in the network.
- When they did it.
- How they did it.
If an intruder hacks 1 machine and bypasses their anti-virus, you can work out how they did it and patch all the other machines before the intruder has a chance to attack again.
Now we have a good handle on what Crowdstrike is and why they’re special, let’s dig into my favourite topic….
🤑 Financials
Firstly, I must give major props to Crowdstrike 👏 They offer an Excel download of all their financials, key performance indicators and more!
Data taken from 2021 to 2017
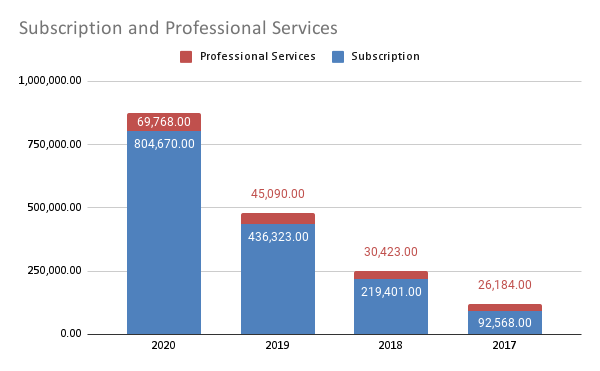
Total Revenue: 874,438 (95% year on year growth)
Professional Services: 69,768 (40% year on year growth)
Subscriptions: 804,670 (106.7% year on year growth)The first thing we notice is that this business is still in its hypergrowth stage, an excellent candidate to analyse. 92% of its yearly revenue comes from the subscriptions they sell to customers, and only 8% from professional services.
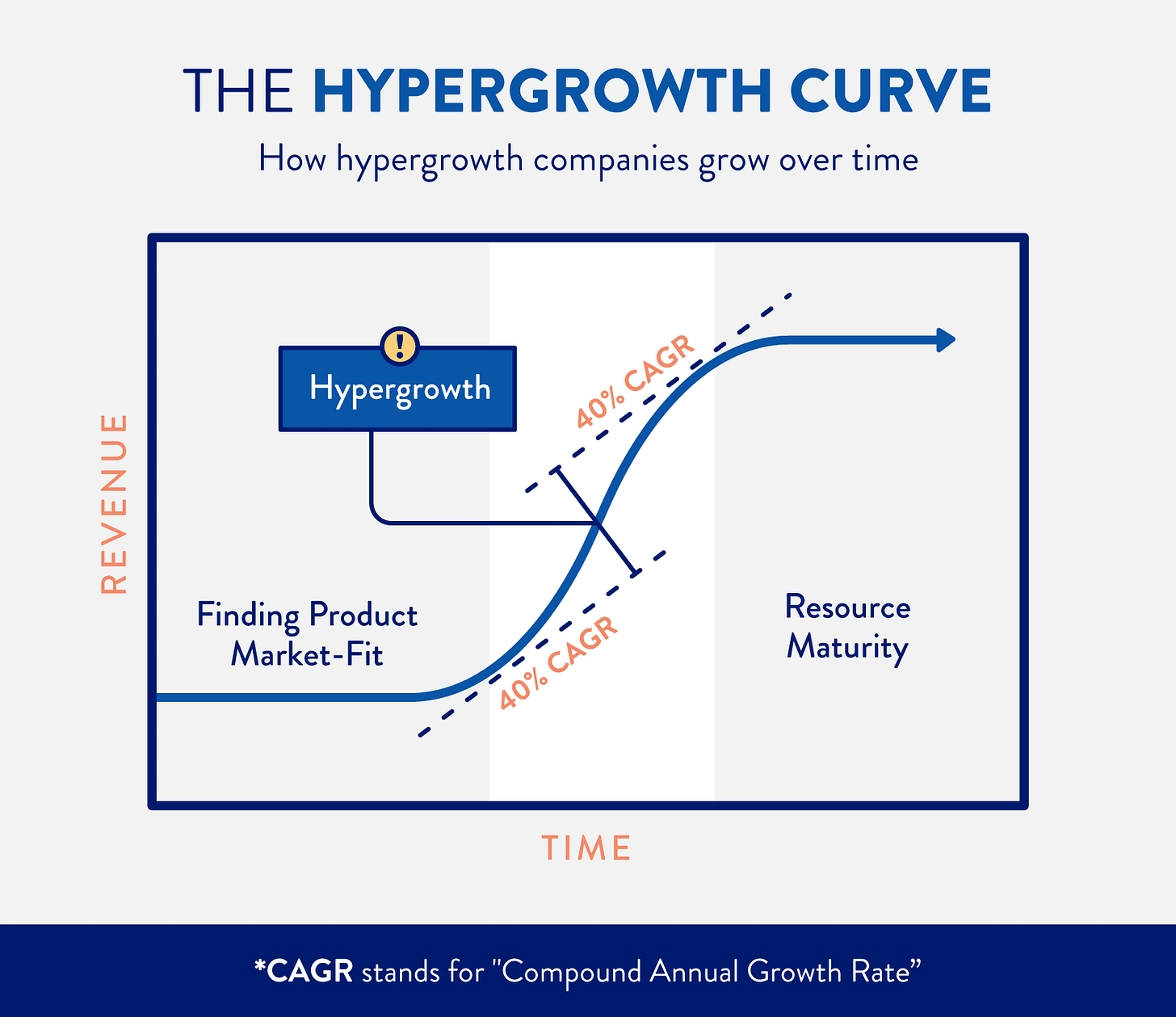
Hypergrowth is what happens when you provide customers with a product or service that they need, but weren’t being served with. Specifically it is the movement from finding product market fit to being mature.
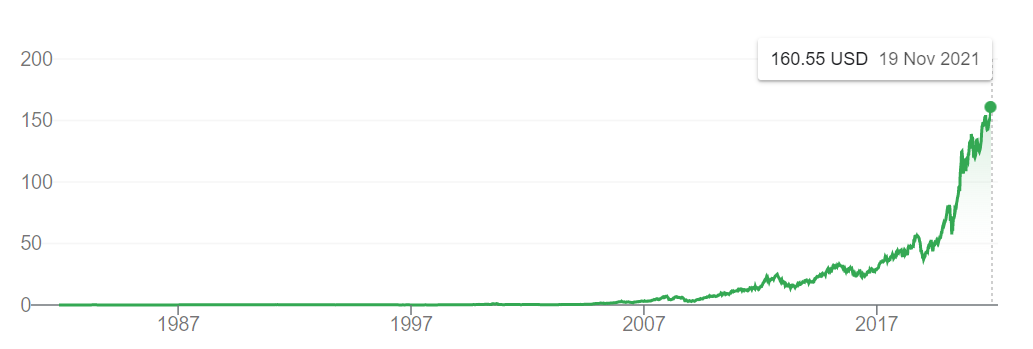
A great example of this is Apple, who were trying to find things they were good at until they released the iPhone in 2007. Ever since then they’ve been experiencing hypergrowth, with their stock doubling nearly every year (more so in the recent years).
Once you find product market fit, the company explodes. Hypergrowth (CAGR over 50%, for me) is proof that the company has a great product that is solving a need for customers, and that has the operational know-how to create and sell it. We don’t need to read the product spec to know this is a great product and people want it. We can see it reflected in the growth.
Ideally with hypergrowth companies we want to see them expending almost as much as they are making, reinvesting it back into the company to continue this 🚀 upward trend. How much does Crowdstrike spend on making this revenue?
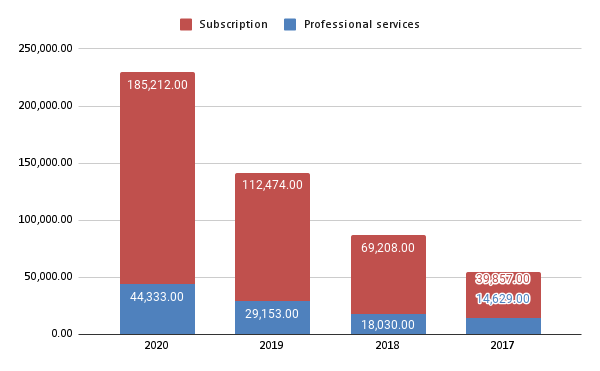
Subscriptions: 185,212 (66% year on year growth)
Professional Services: 44,333 (45% growth)Crowdstrike is increasingly spending more & more on their subscriptions / services, but it is not increasing as fast as the revenue for these services (other than professional services) and is lower than their revenues.
The amount of subscription customers increases each year also:
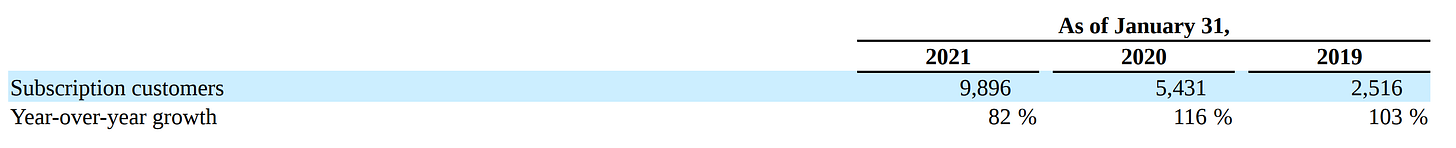
What’s even greater to see is that Crowdstike uses a land-and-expand method. You land a customer with one or two products, and then over time the customer increases their usage.
As of January 31, 2021, subscription customers that had adopted four or more modules, five or more modules and six or more modules increased to 63%, 47%, and 24%, respectively. Our dollar-based net retention rate, which measures expansion in existing customers’ subscriptions over a 12 month period, was 125% as of January 31, 2021, demonstrating the power of our land-and-expand strategy.
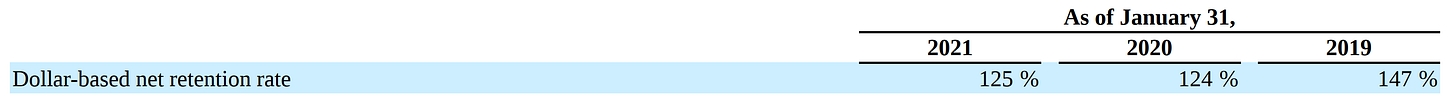
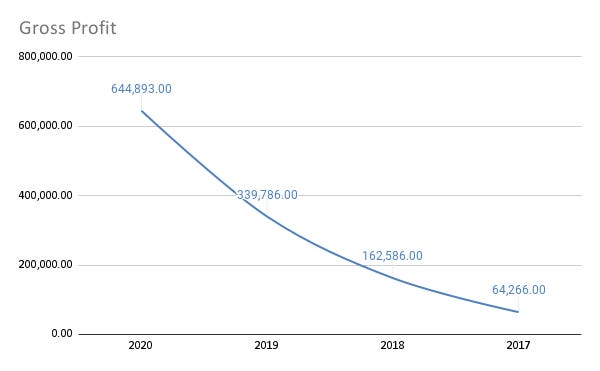
Despite their cost of revenue also experiencing hypergrowth, their gross profit is increasing 117% every year on average since 2017.
I expect professional services revenue to increase in the coming years. This is because Crowdstrike is often used by security operation centre analysts (SOC, or NOC for network operations). Some companies do not have a SOC, so they often delegate the tasks to other security people. In the event of an attack or worse, if the company does not have the rightly trained people they will have to reach out to Crowdstrike to help.
Even if they were trained in sophisticated attacks you’d need specialist help. Solar Winds is a major cyber security company specialising in security monitoring (like Crowdstrike). Major firms like Microsoft and top secret government agencies used Solar Winds products, products such as Threat Monitor — their Crowdstrike competitor. But when they were hacked, they installed Crowdstrike and asked for help, If that isn’t a glowing endorsement of Crowdstrike’s product and their professional services, I’m not sure what is!
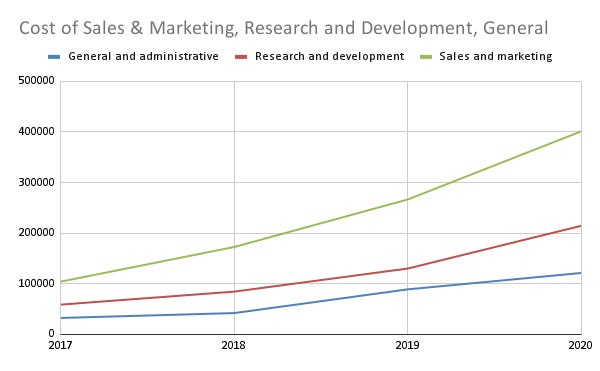
Sales and Marketing: 401,316 (56% growth)
Research and development: 214,670 (54% growth)
General and administrative: 121,436 (59% growth)
Total Operating Expenses: 737,422 (55% growth)It’s absolutely great to see them reinvesting more back into their business, even on frivolous things like marketing. As a wise man once said:
If you can grow 5 customers / day by spending £1, imagine how much you can grow by spending £100!
For technical tools like CrowdStrike, Datadog, Cloudflare, Netlify it’s hard to understand the appeal straight away, it’s often best to hire developer advocates or other similar roles to let people know what you can do on these platforms.
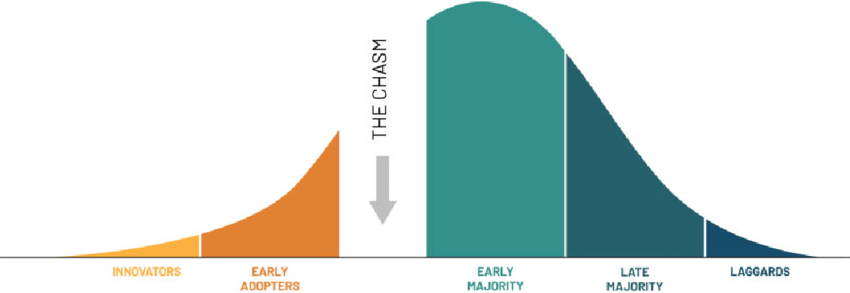
The Chasm is a model of startups. You have the innovators (less than 0.1%) who love using new tech and helping shape it, like those who hang out on the companies forums.
Next up are the early adopters. Those who are not afraid to invest in early technology and can see its advantages, or where it will go.
Then you have the chasm. This is where startups die. The innovators and early adopters are only a small percentage of the total population, you will not reach profitability or renown without crossing the chasm and getting the majority.
The early adopters & innovators have their noses to the ground looking for the next big thing. The early majority & higher wait for you to show them what your product is about, and how it can fix their problems. There are many ways to cross the chasm, Crowdstrike appears to be attacking this at the marketing / sales angle.
This isn’t a controversial method, many companies do this. Even Amazon does this! The 2 main methods to do this are:
- Make it as painless as possible to switch to your product.
- Show customers why your product is superior.
Crowdstrike is experiencing hypergrowth because it is crossing the chasm.
Their growth results in a net loss of…
Net loss: -92,629 (decreasing 10% year on year)Which is impressive. For startups typically the cycle is:
- Get venture capital funding (or crowdfunding!).
- Spend it all on improving yourself.
- If you make profit, that profit goes back into the business.
- Ideally you should be losing money or not making any money, VCs are happy to invest in startups that lose money so long as they expect a 100x or higher return within an appropriate timeline.
In the video game Plague Inc, the easiest way to win is by infecting everyone with no symptoms and then once it’s done, strike the hammer and mutate to involve symptoms.

The same is true for startups. It is significantly easier to get customers to use your services when you don’t make profit, and even easier if you lose money. Venture capital funds are more than happy to invest in loss-making businesses if they can see a 100x return in 10 years or so.
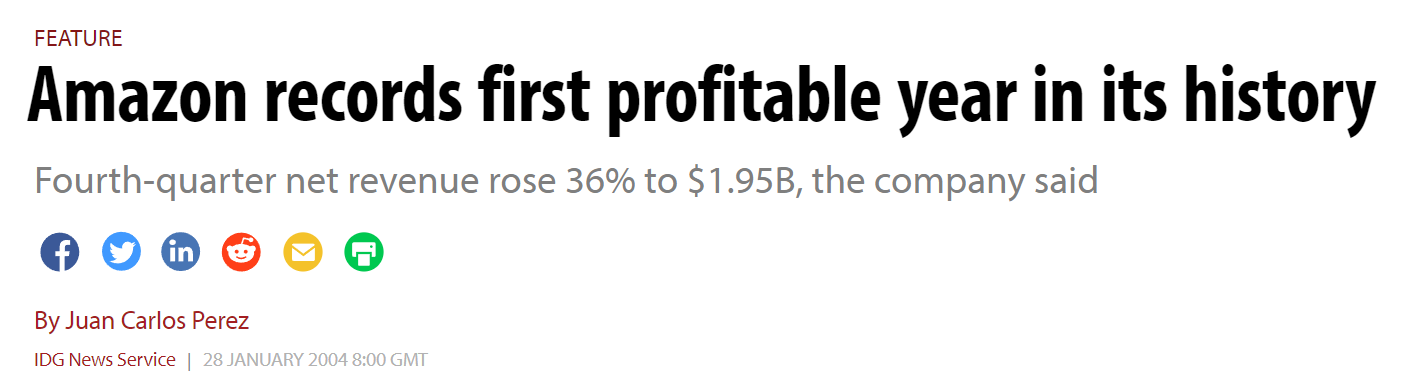
Amazon, founded in 1994, was already a multi-billion dollar company by the early 2000s. It was only 2004 that they first made profit, and even then it wasn’t a lot compared to how much they spent. To an ordinary investor companies losing money is ridiculous, but we can and should see Crowdstrike is losing money because they are expanding, growing, and fighting for the market share on more fronts every year.
Typically when a company is loss-making I hope to see an invisible switch. The company flicks this switch and poof! It is suddenly profit-making (but substantially decreases its growth prospects). An example of this is Disney Plus. They can charge you more money for it. If you want to watch Disney, what are you going to do? Your options are vastly inferior compared to just paying more. Once you built a moat during pre-profit years, you can flick the switch to make profit without risking customers leaving.
We’ll explore if Crowdstrike has a switch later on and what their moat is like.
Let’s look at their balance sheet now.
Total Assets: 2,732,533 (139% growth)
Cash: 1,918,608 (225% growth)
Total Debt: 1,860,659 (75% growth)
Current Liabilities: 863,553 (73% growth)Crowdstrike is experiencing massive growth in its revenues, so much so that nearly doubling their debts every year pales in comparison.
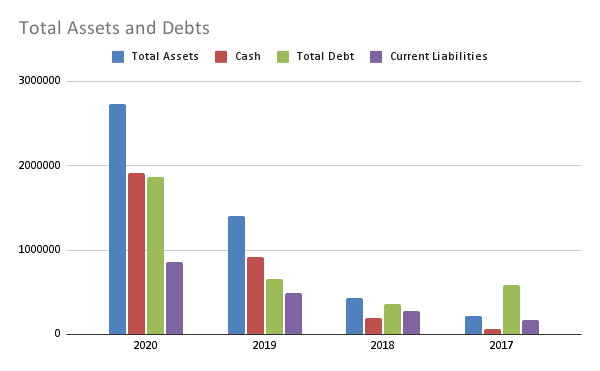
Fortunately their total debts never exceed the amount of cash they have, apart from their earlier years. Their assets, especially cash, is growing exponentially more than their debts which means it’s unlikely to outpace their debts.
Let’s take a look at their cashflow now.
Operating Cash Flow: 458,972 (220% growth)
Financing Cash Flow: 804,499 (83% growth)
End Cash Position: 1,786,408 (214% growth)
Free Cash Flow: 364,247 (604% growth)Something to be wary of is that they went from having very little (sometimes negative) flows to incredibly large amounts of money, making some of these percentage gains awfully high.
The operating cash flow (how much they make from regular business activities) is lower than their financing cash flow (how much they make from funding). This is because Crowdstrike has been funded a total of 7 times.
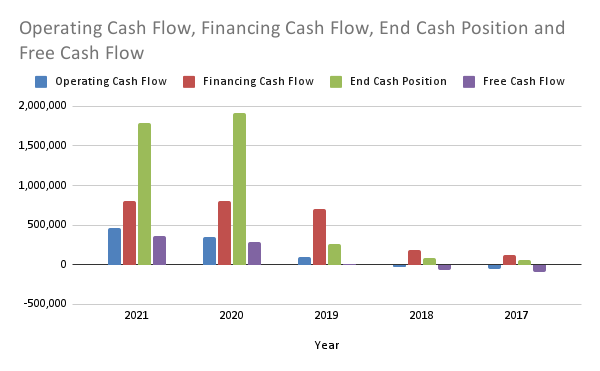
The cash they generate from business is growing incredibly fast, eventually, this will hopefully dwarf the money they raise from financing. Their last investment round was 2018, 3 years ago. If they needed a cash injection they would seek another round, it is great that they aren’t. This indicates they are crossing the chasm as they do not need to rely on venture capitalists so much.
While they have a lot of cash, their free cash flow isn’t as high (although it is growing). This is a great sign that the business is still investing in itself.
To me, their finances look absolutely on fire 🔥 and they are doing everything right. If you’re interested in big numbers, check out this paragraph I stole from their 10k:
We have experienced significant growth, with total revenue increasing from $249.8 million for fiscal 2019 to $481.4 million for fiscal 2020, representing year-over-year growth of 93%, and from $481.4 million for fiscal 2020 to $874.4 million for fiscal 2021, representing year-over-year growth of 82%. Subscription revenue grew from $219.4 million for fiscal 2019 to $436.3 million for fiscal 2020, a 99% increase, and from $436.3 million for fiscal 2020 to $804.7 million for fiscal 2021, a 84% increase. Our annual recurring revenue, or ARR, has grown from $312.7 million as of January 31, 2019 to $600.5 million as of January 31, 2020, a 92% increase, and from $600.5 million as of January 31, 2020 to $1.1 billion as of January 31, 2021, a 75% increase. We had net losses of $92.6 million, $141.8 million, and $140.1 million in fiscal 2021, fiscal 2020 and fiscal 2019, respectively. We expect to continue to incur net losses for the foreseeable future as we continue to invest in our business, and in particular, our sales and R&D capabilities, to address our large market opportunity
🦅 Products
Let’s take a look at their products now, it can bee confusing if you don’t work in this industry — which is exactly why I love investing in these companies! Peter Lynch, Warren Buffet, and all the greats avoid technology stocks because they don’t understand them. I understand them as I work in this field (quite literally — I actually work with these products on a daily basis).
I’ll try my best to explain the products 🤓
🕊 Falcon - Endpoint Detection & Response
We’ve already discussed this, but let’s go further. The base data retention is set to a maximum of 90 days, meaning if you get hacked 91 days ago you cannot use EDR to identify the attackers. However! You can use the Falcon Data Replicator to offload the data to the cloud.
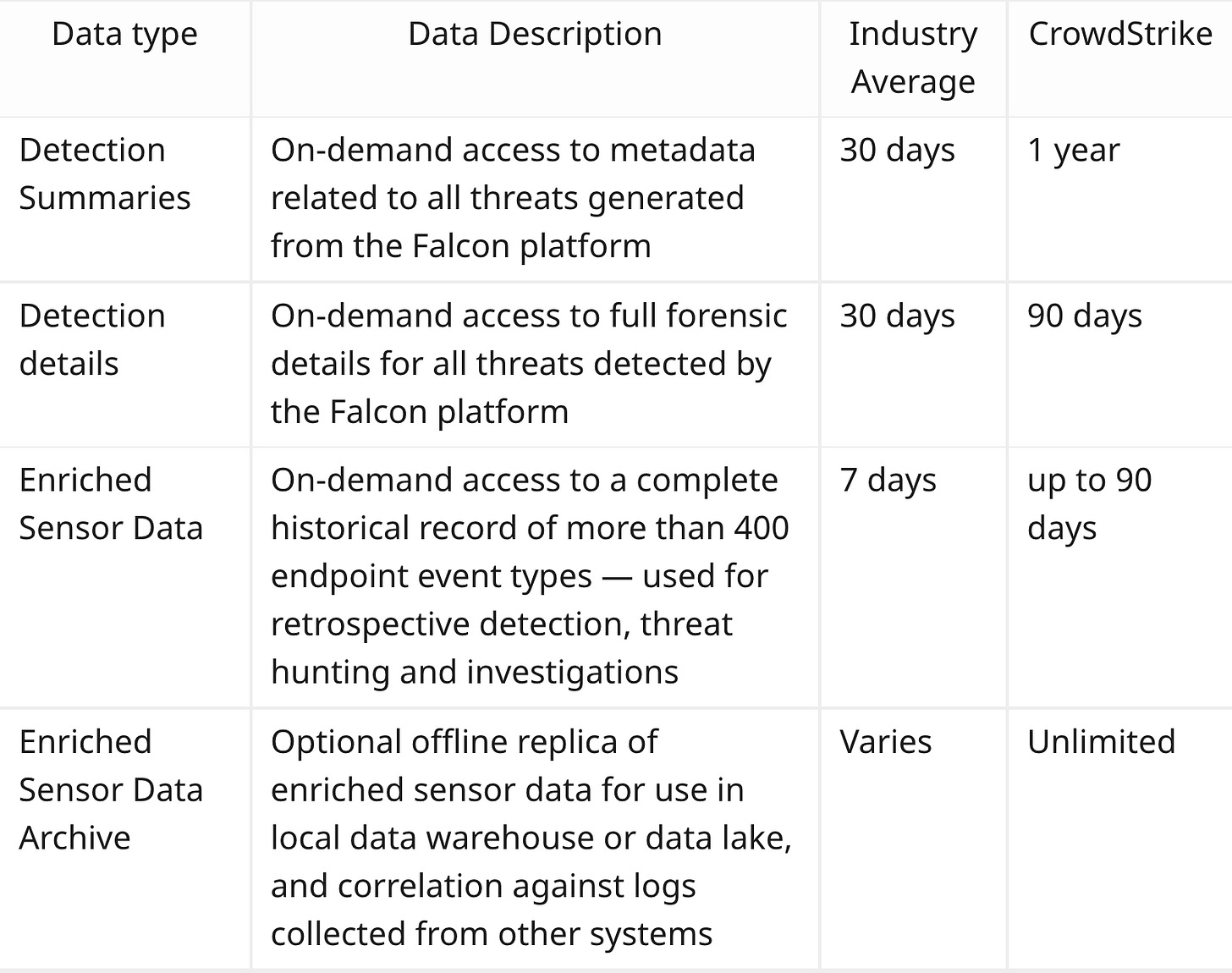
This is a free tool that anyone can use, but they also sell it as an add-on. Presumably for companies without the technical know-how to export to S3 themselves. There are also a load of exporters for Security Information & Events Monitoring (SIEM) tools. These tools take this data, you can create “alerts” on things that have happened or can view & analyse the data.
Something you’ll notice is that Crowdstrike is a-okay with exporting the data or using it in other tools. I personally like this as “one-size-fits-all” solutions generally suck, but mix-and-matching them allows organisations to find the perfect combo (or you can just use the defaults Crowdstrike provides you).
There’s actually a bunch of services offered under Falcon:
Endpoint Security Solutions
- Falcon Prevent — Next Generation Antivirus (NGAV)
- Falcon Insight — Endpoint Detection and Response (EDR)
- Falcon Device Control — USB Device Control
- Falcon Firewall Management — Host Firewall Control
- Falcon For Mobile — Mobile Endpoint Detection and Response
- Falcon Forensics — Forensic Data Analysis
Security & IT Operations
- Falcon OverWatch — Managed Threat Hunting
- Falcon Discover — Security Hygiene
- Falcon Spotlight — Vulnerability Management
Threat Intelligence
- Falcon X — Threat Intelligence
- Falcon Search Engine — The Fastest Malware Search Engine
- Falcon Sandbox — Automated Malware Analysis
Cloud Security Solutions
- Falcon Cloud Workload Protection — For AWS, Azure and GCP
- Falcon Horizon — Cloud Security Posture Management (CSPM)
- Container Security
Identity Protection Solutions
We don’t need to learn all of these to figure out if this is a good company to invest in, but here’s a few of my favourites:
This is EDR for the cloud. Taking from their services site here are my favourite features:
- Gain visibility into container environments: Get full visibility into running containers to uncover details surrounding file access, network communications and process activity.
- Identify vulnerabilities faster: Save valuable time with pre-built image scanning policies enabling you to quickly catch vulnerabilities, misconfigurations, and more.
- Accelerate delivery: Create verified image policies to ensure that only approved images are allowed to progress through your pipeline and run in your hosts or Kubernetes clusters.
Generally there is no EDR identification on pods in Kubernetes at most organisations, the closet you’ll get is the ELK stack (Elastic, Logstash, Kibana) which can be made into a SIEM-like tool. The idea of having security monitoring over Kubernetes is very cool, and I like the verified image policies. I’ve seen quite a few attacks where you can deploy images to Kubernetes that aren’t meant to be deployed 😅
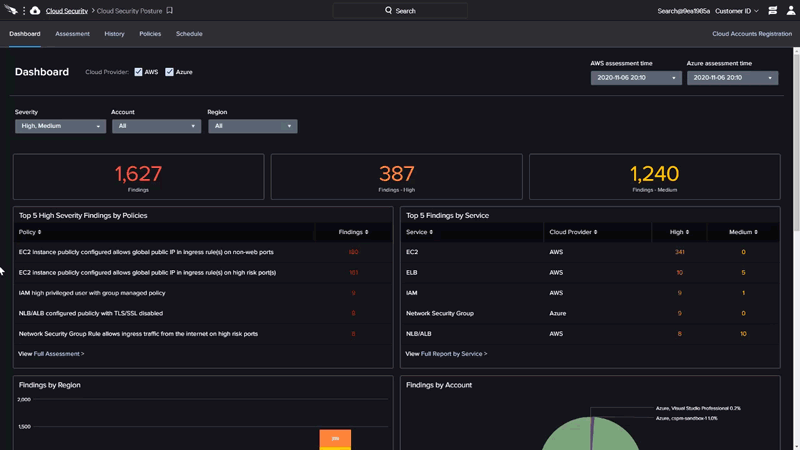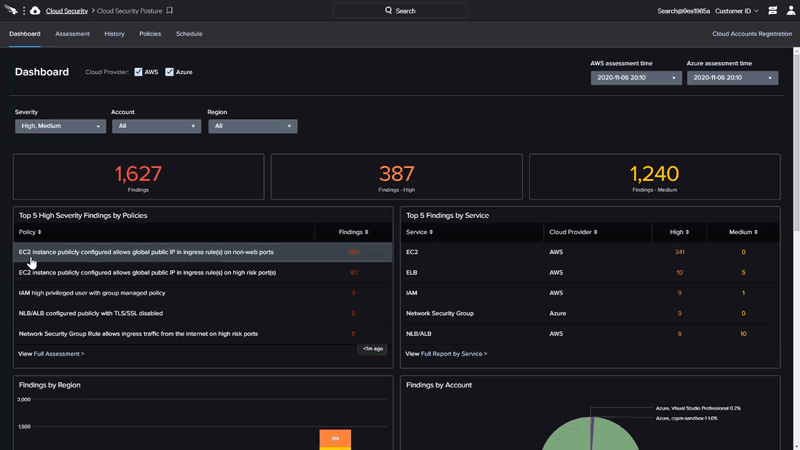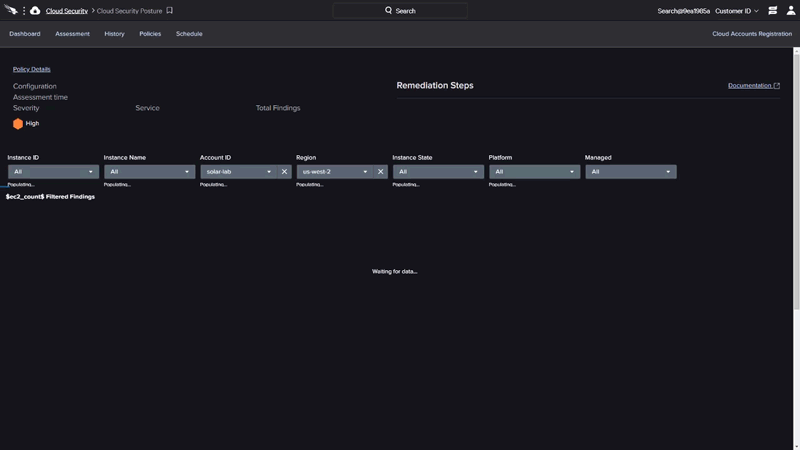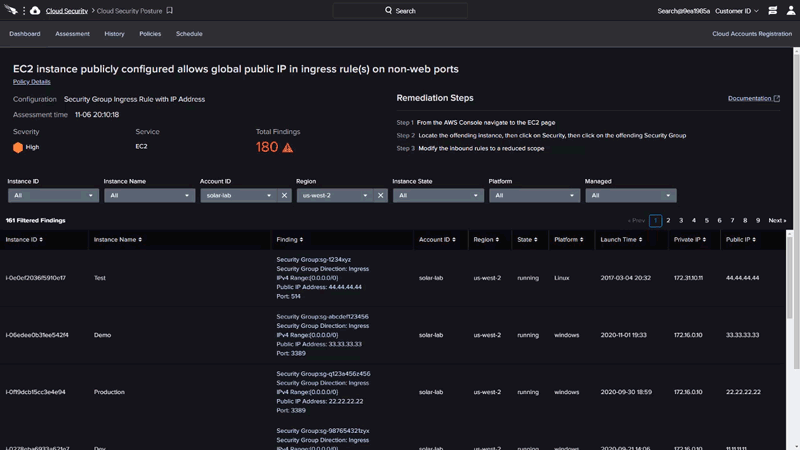
Their next service I like is Falcon Horizon Cloud Security Posture Management. This finds misconfigurations in cloud deployed resources. I haven’t used this, but I’d hope to see this done at pull request time by reading the infrastructure-as-code like Snyk does.
😴 Okay this is probably quite boring for you, but the point I am trying to make is that I am reading these products and thinking:
“Huh, that’s neat. We should use this”
Their products, while varied, are genuinely useful and innovative. The next big question is are they good? From my personal experience I can say that Crowdstrike is very good. Sentinel One caught more viruses, but it uses a lot of memory (Crowdstrike uses very little memory). The reports weren’t also very good, and I didn’t like the support so much. But don’t take my word for it, this video shows you Crowdstrike up front:
The TL;DR of this 2019 video is:
- Crowdstrike uses very low resources.
- It doesn’t catch all the viruses.
I found it was exactly the same. At the time of execution it didn’t find all malware, however after a few hours or so it’d report back about the malware. I think if it thinks that a piece of software isn’t immediately dangerous it’ll upload it to the cloud so it can process it some more before telling you.
Security vs availability is a see-saw. To have maximum security you need to the system to be highly unavailable. It’s very easy to block all software, like Google Chrome, so it never has malware. The amount of times I’ve coded programs for them to be blocked as “viruses” is too high!
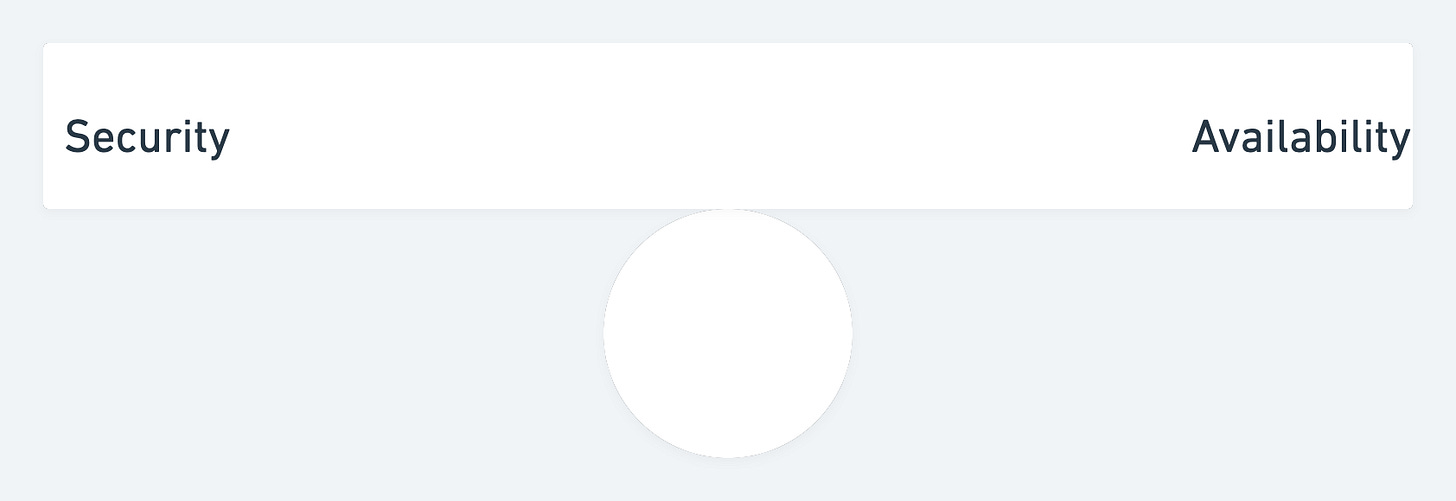
Crowdstrike balances this quite well. It doesn’t get all the viruses at run-time, but it also doesn’t get into the users way — and it will eventually get the viruses.
Compare this to Sentinel One, Crowdstrike’s biggest competitor:
I also had the same experience as this 2019 video. Sentinel One was overly aggressive, it would block legitimate programs. It was also a CPU hog, slowing my entire system down and was very noticeable.
Whereas Crowdstrike is more available, Sentinel One is more security focussed. In my opinion I’d rather not get in the users way and have a small virus, then to constantly bother the user. If everyones computers in an organisation slowed down by 20%, and they couldn’t even run legitament software the revenue of the company will decrease as they can no longer work easily 😅
Something to note here is that it’s very easy for someone not in this industry to see the anti virus at the product. It is not. The end point detection & response is the product. If a hacker wanted to create a virus to destroy your company, they can. They’d use a zero-day and no anti-virus on the planet will ever be able to tell. The hard part is tracing, identifying, reporting and mitigating that in the future.

Don’t get me wrong, the next-gen anti virus is nice. But it’s not the main reason people look at these products. You can invest in all the anti-viruses you want, but at the end of the day your users will download random software and mess it all up for you.
File Vantage
File Vantage is a solution for monitoring files. Imagine this. You have thousands, millions of files and you need to know:
- Who accessed it.
- When.
- Where did they access it from?
- What did they do with the file?
As you can imagine monitoring all of this just sucks. Like straight up sucks. There are so many files, monitoring all this info will kill someones laptop. But, you have to do it. Regulatory authorities require you to monitor these important assets. Insider threats are where employees change, distribute, or otherwise harm files they are not meant to be touching. They could secretly be selling data to other companies, or harming your company.
These file monitoring programs are designed to protect against this, but companies often build their own solutions as all the ones on market suck. Crowdstrike built their own solution, File Vantage.
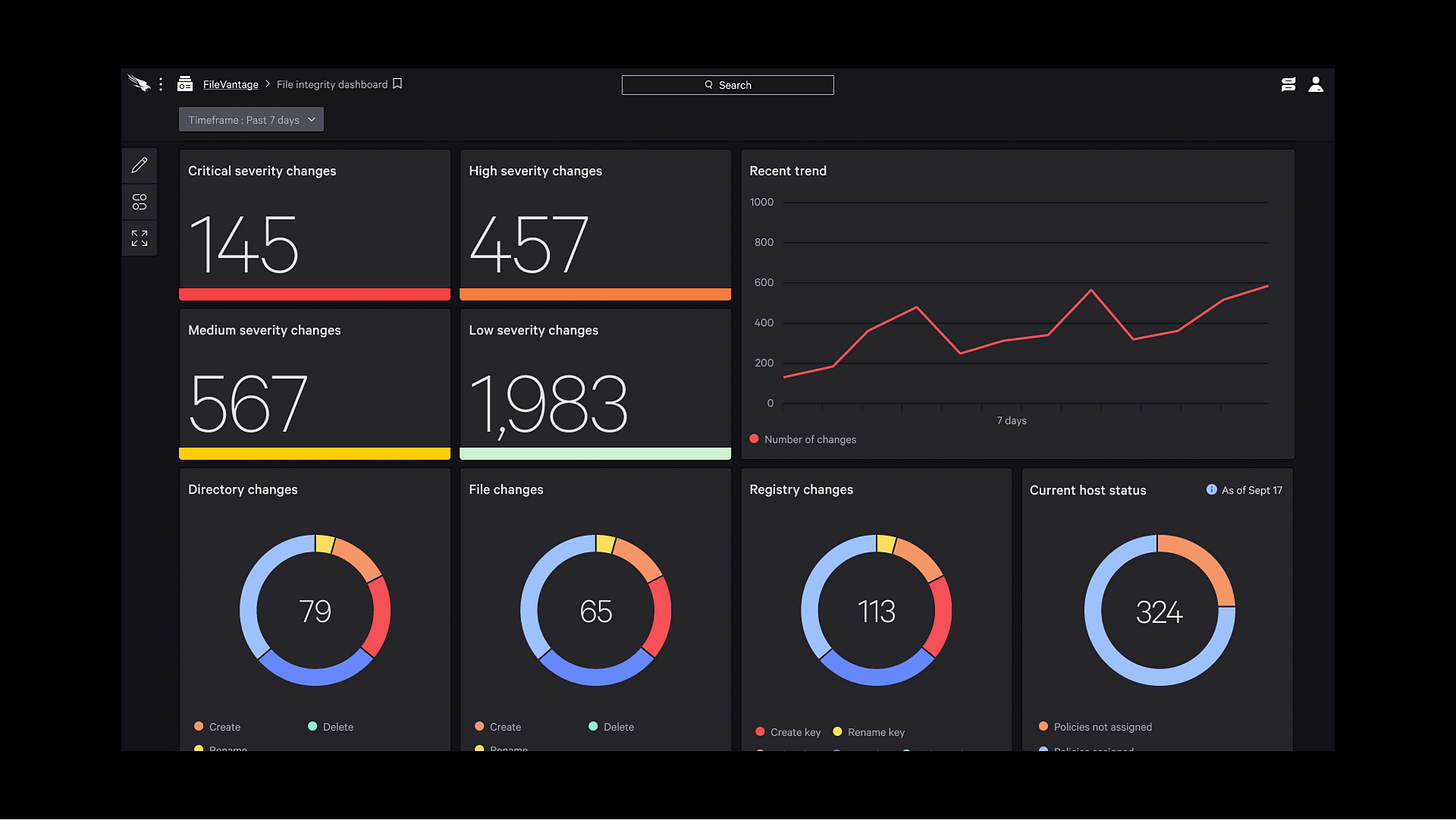
Not only does Crowdstrike give you the important information but they built it into the Falcon platform. They allow staff to quickly target file change data with relevant adversary activity, offering added insights with CrowdStrike’s threat intelligence data. Not
This is a great example of something Crowdstrike probably built in-house to serve themselves, and then sold as a product.
ExPRT.AI, Spotlight
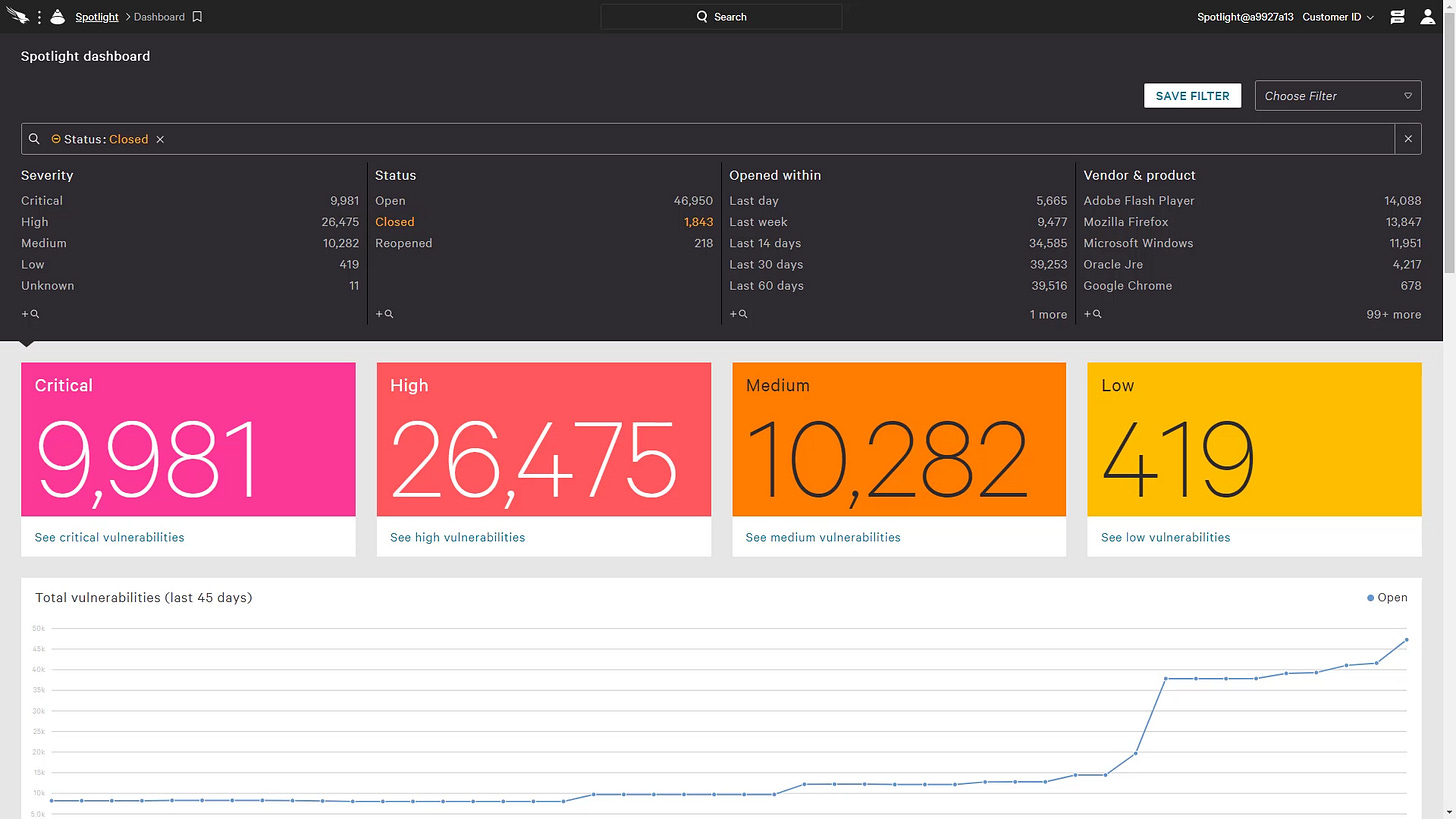
Companies have thousands of vulnerabilities a month. Literally thousands. I’m not kidding, I get maybe 200 - 300 a week in my inbox and I don’t even work in security! These alerts are so ridiculous. I once had an alert for a floppy disk drive vulnerability. We don’t even have a floppy disk drive? What I’m trying to say is that I’ve spent so many hours of my time just figuring out which vulnerabilities are important and if I need to patch them.
If everything is a priority, nothing is
Crowdstrike Spotlight uses an AI model (called ExPRT.ai ) to determine what the priority is. If you pay a developer £100k and they spend 20 hours a week prioritising vulnerabilities (not even fixing them, I kept that for another week), you’re looking at about £260 / day just for that.
Up that to 40 people (depending on size of company, I am guessing here) and you have £10k a day in just paying people to read documentation and try to prioritise the worst vulnerabilities.
Crowdstrike does that for you automatically, so it is automatically worth £10k / day. This is just a no-brainer for companies (and please I would love this at my company).
In Crowdstrike’s Investor Product Briefing they hinted at automatically fixing some of these vulnerabilities too. I am guessing because they have agents on all the machines it is easier for them to edit or update software.
If Crowdstrike can even pick off 5% of all the vulnerabilities I get in my inbox I will be infinitely happy.
🏝 Workflows
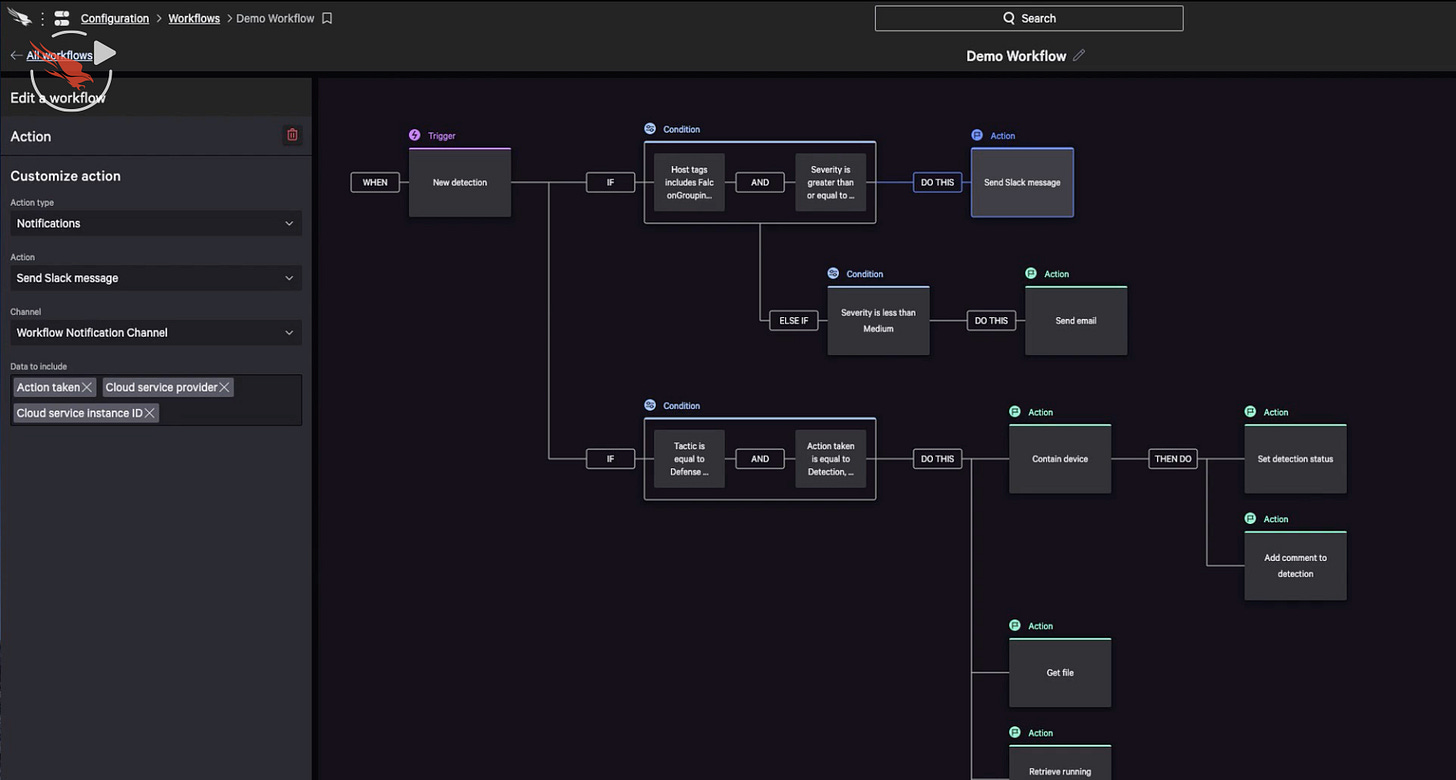
Not much to this other than look! You can build workflows. This reminds me of Zapier. Spot an incident, report it to Slack or email it, tag it, isolate the device and so on. Complex workflows that automate away the boring parts of incident management.
📊 Threat Graph
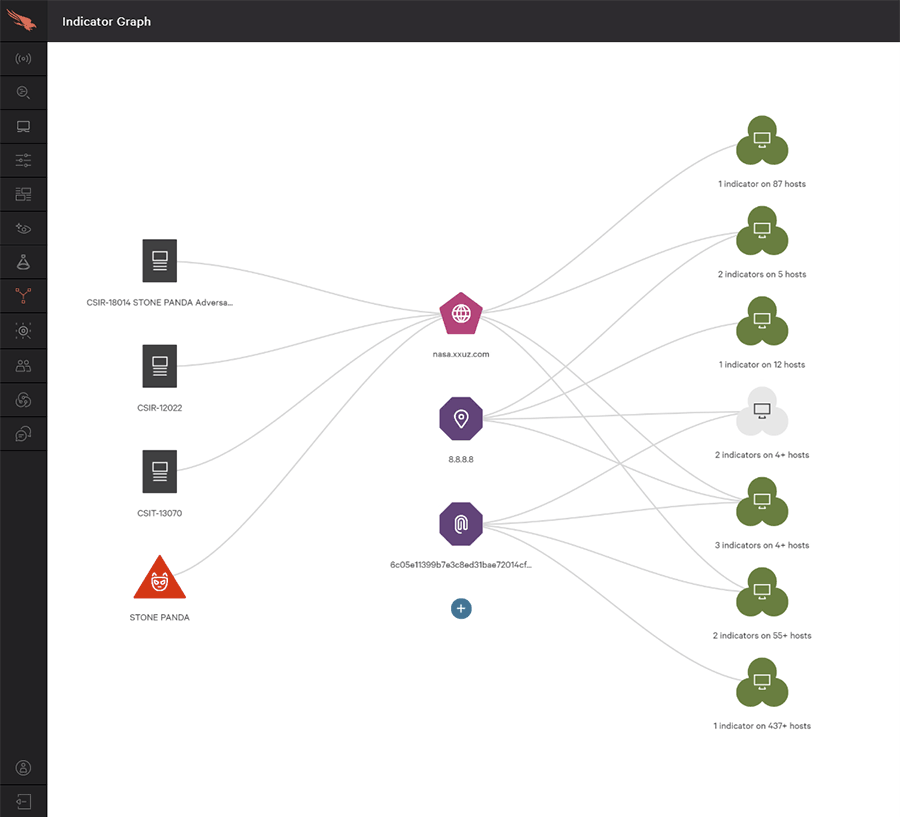
When you have an event, you can follow a graph to visualise the relationship between endpoints, indicators of compromise and more. Here’s a good video on this:
To save you some time, in the above video Crowdstrike prevented a file called evil.exe from running. There are some cool things:
- It tells you who the file is associated with, in the video it’s with Cobalt Spider who targets financial groups. It’s more common to come across files or attacks from advanced persistent threats than you think.
- We can view network activity to see where it attempts to communicate to.
- We can see what threat actor and file are associated to what hosts, where it came from and more.
The TL;DR is that this is really cool, and an absolutely great benefit to the company. Like I said, if someone wanted to hack you they will. The hard part is figuring out how they did it, what machines are affected, and creating a report to show your seniors and any data protection regulatory bodies.
🎢 Security Cloud Loop
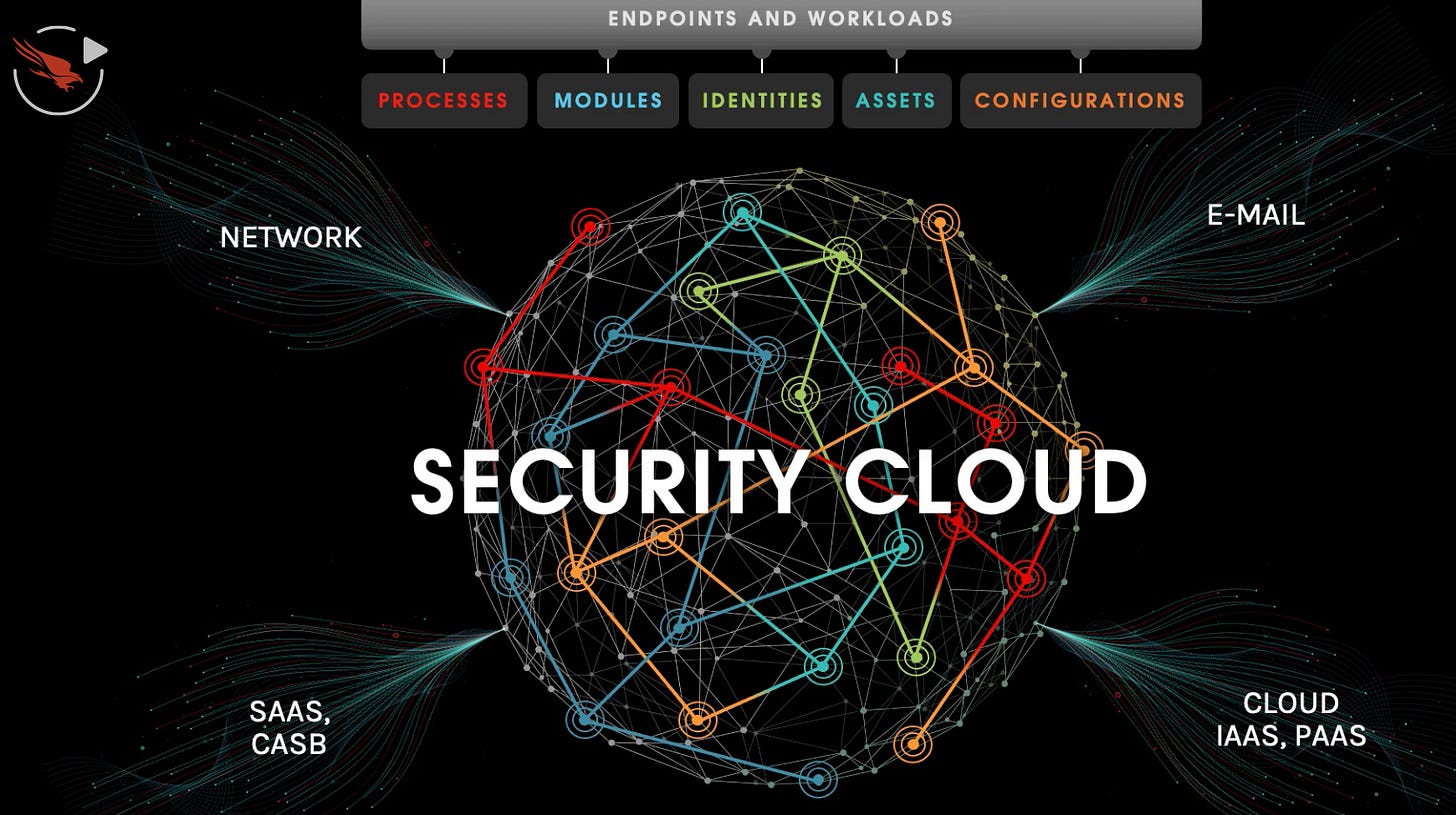
😕 People don’t know what they do
One of my favourite things is to invest in companies that the average person can’t understand yet. I love reading comments about these companies like “what’s so special about them? They only do X. And you can replace X so easily. Very competitive.”
In Crowdstrike’s place, this is “what’s so special about an anti-virus?” The average investor does not understand enterprise cybersecurity, which gives people like me who implement enterprise cybersecurity an edge.
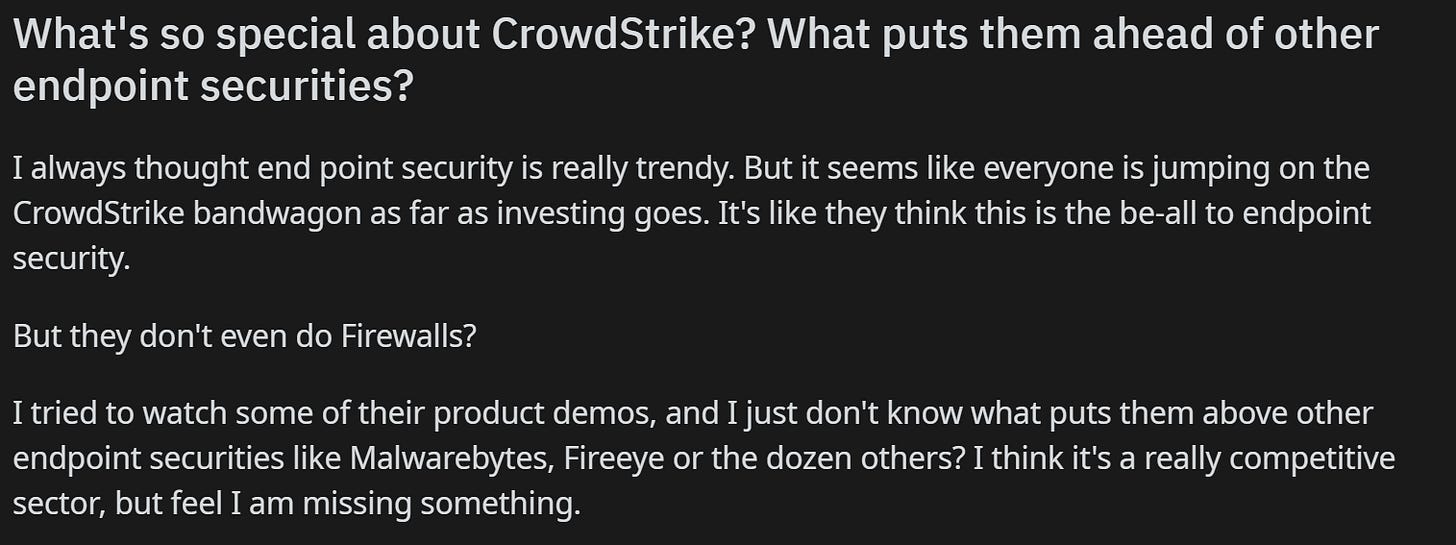
Comments like these make me so happy. You don’t tend to put firewalls on individual PCs, you put them on the network level so all ingress / egress traffic on your network goes through a firewall. And comparing it to Malwarebytes? Again — they think this is just an anti-virus product.

Even better when industry professionals do not see the point. Having an anti-virus is important, but if a hacking group wants to hack you they will. And no matter how good your anti-virus is, Karen from Accounting will always download some file which is obviously a virus and run it regardless. Training your users is one of the hardest parts of security.
Something to note also is that Crowdstrike does have a moat. Companies may choose to invest heavily into Crowdstrike and integrate it rather deeply.
🥊 Competitors
🤖 Sentinel One

I think Sentinel One was a bit immature. They were over-zealous in their anti-virus, and their alerts weren’t so useful. For instance, if I wanted to make an alert and see if that would have fired in the past I couldn’t. Crowdstrike I could.
I think Sentinel One poses a real threat to Crowdstrike, but I’m not too concerned. A rising tide lifts all boats.
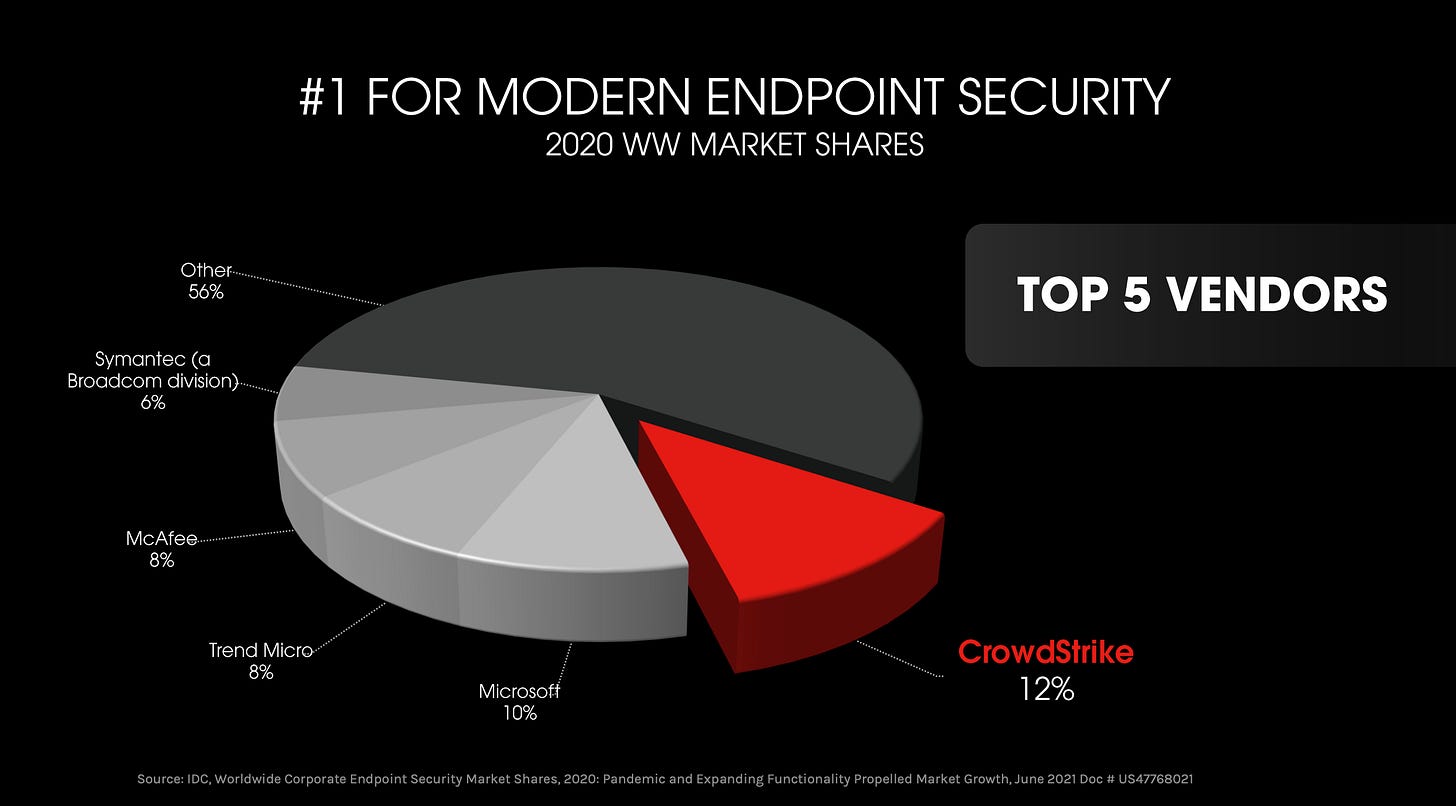
Crowdstrike currently has the market share for endpoint security, and Gartner reports that Crowdstrike is one of the leaders in this space:
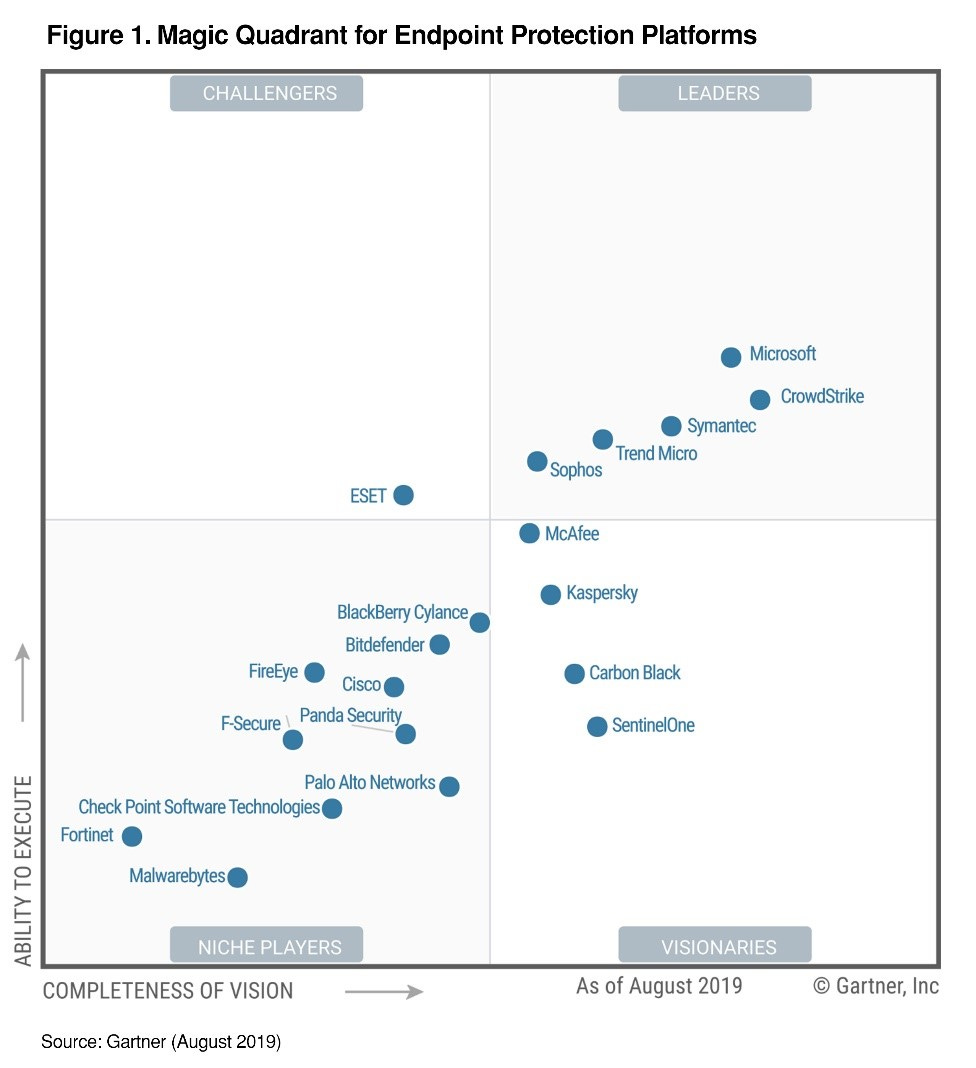
Notice how they call Sentinel one a Niche-Visionary player in this field. I think Sentinel One could be a serious competitor, but I think it’s incredibly unlikely that one prevailing company comes out on top.
🤾 Microsoft
I actually didn’t know Microsoft did endpoint detection until I wrote this article, and I interviewed there 😅 As you can guess if you are primarily a Microsoft-based company (Azure and Windows) then you’ll have deep integration with Microsoft’s endpoint security. This helps achieve better stability & performance, which as we saw earlier is very important.
As you might be able to guess this is Windows only. You need active directory or Azure active directory for devices to be discovered, meaning that unless a company is 100% Windows it will not be effective. They do have some workarounds for this, however:

Giant red boxes that say “Caution” and “if [Linux] is an absolute requirement in your environment…” does not bring me hope that this works very well. Indeed the install instructions are very difficult.
I think Microsoft has the capacity to eat Crowdstrike, quite literally — they could buy them. But I’m not confident that in the near future their endpoint security will please the security people, especially when said security people often love Linux or Mac OS.
Andy Malone is a Microsoft MVP which is a synonym for professional Microsoft shill who doesn’t get paid for it, if you watch the above video be mindful of that bias. Here’s somethings I picked up that may be interesting:
- It appears only Windows 10 and higher works. I am willing to bet a lot of organsiations do not use Windows 10 :(
- It’s quite confusing. You appear to have to configure everything. Want to scan downloads? Network monitoring? You have to turn this on. So by default it appears to do…. nothing.
Okay I stopped watching the video about halfway through, I honestly do not see myself using this product and I am supposed to be the customer they are targeting this at 😅 It looks so complex and everything looks turned off by default. Why would I use that when I can use literally anything else?
🎖 What is the future of Crowdstrike?
Crowdstrike has an interesting approach to new products. Because they already have agents on all the devices it is easier for them to ship new software to create a new product. And because they already have all the data in the cloud they can use this to improve the experience.
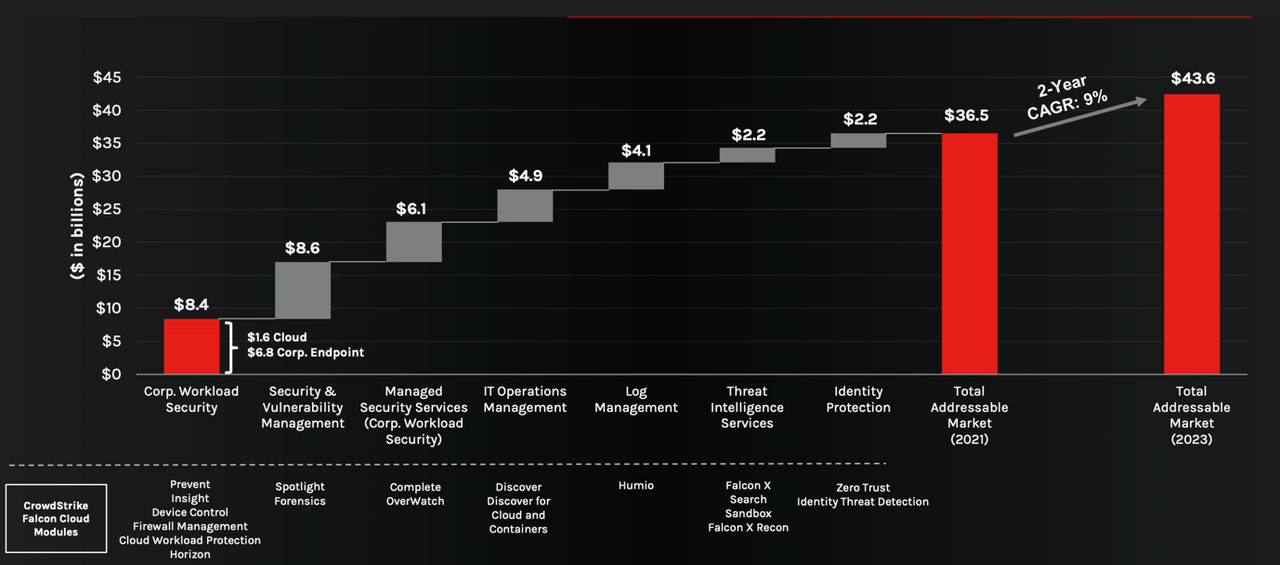
Crowdstrike is adding cybersecurity-adjacent products at a rapid pace, and these products often solve headaches for the users. Something I noticed is that they are expanding into log management with their acquisition of Humio.
There is a lot of competition in log management & monitoring.
I think this expansion makes sense, however. Crowdstrike already has logging agents on all the machines so there’s nothing special there. They upload their logs to the cloud, and Crowdstrike can analyse them. What I’m excited about is seeing Crowdstrike leverage its data and creating a machine learning model for the logs. If they could flag loglines which are potentially malicious that’d be interesting.
When we began discussions with CrowdStrike, we instantly saw the power the two companies could bring to customers. With Humio, CrowdStrike accelerates the extraction of value from data by enabling customers to collect all of the data in real time and at scale. As an industry leading data platform, CrowdStrike will leverage Humio's streaming analytics to power cloud log management to redefine XDR.
The great thing about more data is it creates a moat around your company. It’s unwise to compete with Cloudflare because they have a lot of data on how the internet operates. In the same sense it may be unwise to compete with Crowdstrike.
According to IBM the cyber security industry is growing every year at a rapid pace.
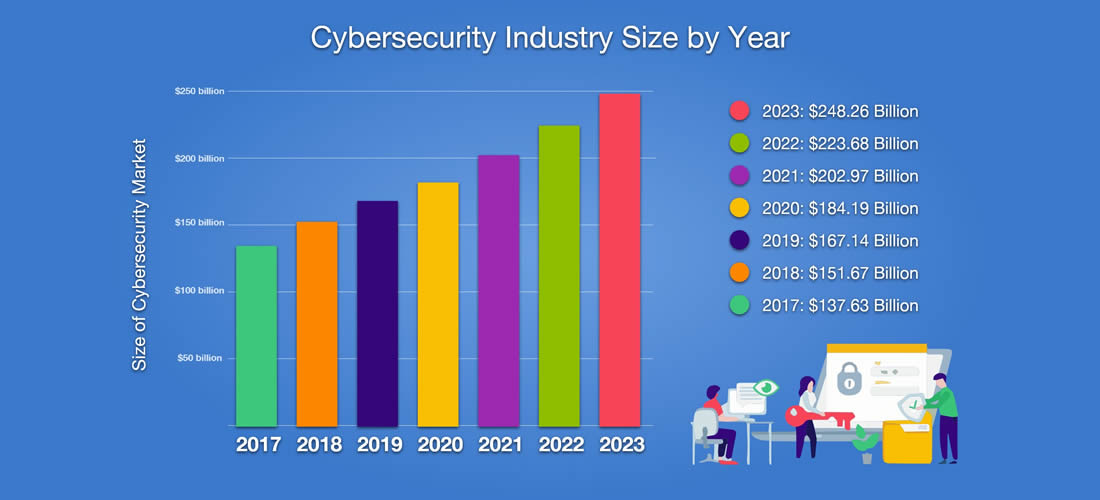
Every year hackers get more & more sophisicated, they rake in more money and cause more problems. As the blackhat hacking industry grows I predict that in 5 - 10 years the only ones who stand a real chance of stopping them are the ones that have been collecting data. Data allows you to create highly accurate artificial intelligence models which could see the hacks as they are happening.
Overtime Crowdstrike’s core product will only improve with more data. I’d like to see them move more into the identity domain, specifically Single Sign On and compete with Okta.
They already have a product for this, but it’s not a 1:1 feature match of Okta (another company I love). Specifically I would love to see them leverage their data to detect if a user is who they say they are, like a hidden captcha. An example is if a user who is commonly in the United States suddenly logs in from North Korea it is likely they have been hacked.
🏵 Acquisitions
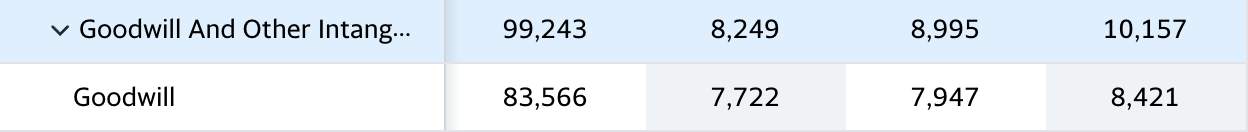
We’ve got to talk about the mergers & acquisitions. Clearly Crowdstrike has some as they hold goodwill on their balance sheet. Goodwill happens when you buy a company worth £10 billion for £15 billion, and your accountants have to explain away the £5 billion difference so they call it “good will”.
🚢 Humio
This is probably their largest purchase yet, or at least the one that makes me go “oooooh”. Humio is a log management platform at scale™️

The TL;DR for the non-nerds is that at scale (like, with 40,000 kubernetes pods, 50,000 machines and so on) logging becomes hard. They install a little agent on your machine and this agent uploads the logs to somewhere. The hard part is that “somewhere”, it has to handle millions of logs / second 😅
Humio is very similar to Datadog / Elastic. It’s literally the same problem. In my opinion this is a great company to absorb. Crowdstrike could do something like continuously read the logs for any malicious activity.
It’s also a really hard problem to solve. Like, so hard I couldn’t do it on my own if I tried. By absorbing another company they’ve reduced the amount of engineering hours needed to create their own solution. Win!
⭕️ SecureCircle
CrowdStrike completes acquisition of @SecureCircleIO to disrupt the legacy DLP Market with next-gen data protection - Read more here: https://t.co/yOoXXtoHKw pic.twitter.com/byzuPsVDHW
— CrowdStrike (@CrowdStrike) November 30, 2021
SecureCircle is a service which extends Zero Trust security to data on the endpoint™️ The TL;DR is that they secure data in transit, in rest and in use all without the users noticing.
What they aim to do is Data Loss Prevention (DLP) — detecting and preventing data breaches, exfiltration or unwanted destruction of data. If you’re a lawyer working on a case then SecureCircle will make sure:
- You can’t accidentally destroy the case files on your machine.
- They’re secured against outsider threats.
- You can’t send those case files to outsiders.
If you want a demo I found this video helpful:
This is something I would personally set up. Crowdstrike is already on all of my endpoints so if I can add some Data Loss Prevention with the click of a button and some extra money spent, why not?
🧸 Bear
- Sentinel One becomes much better and takes over as the market-leader. I’m sure we’ll be able to see this when Sentinel One is deployed for major hacks instead of Crowdstrike.
- Crowdstrike fails to collect enough data and their machine learning models become worse.
- They begin diworsifying and acquiring companies which do not directly add to their revenues or reduce costs.
🐂 Bull
I’m looking for some specific metrics here:
- Number of customers increases.
- The land-and-expand method works, with net-dollar based retention rate increasing.
- Crowdstrike is continued to be used for big hacks, like Solarwind.
- Their stock price dips in the first 2/3 quarters of the year, which is a great time to buy. From their own annual statement:
Given the annual budget approval process of many of our customers, we see seasonal patterns in our business. We expect these seasonal variations to become more pronounced in future periods, with net new ARR generation being greater in the second half of the year, particularly in the fourth quarter, as compared to the first half of the year. In addition, we also experience seasonality in our operating margin, with a lower margin in the first half of our fiscal year due to a step up in costs for payroll taxes, new hires, and annual sales and marketing events. This also impacts the timing of operating cash flow and free cash flow.
I think at some point throughout the year the people with paper hands will likely dump, which sets up a great position to buy thanks to Crowdstrike’s own admission of this.
- COVID ramps up again, because this allows Crowdstrike to grow faster due to the new use of endpoints at home. Per their 10k:
In March 2020, we launched two initiatives to help our customers quickly onboard new remote workers without sacrificing protection or having to worry about a procurement cycle. This included a surge relief plan that allows our customers to surge the number of endpoints for a limited time. Additionally, we launched a Falcon Prevent for Home Use program that allows our customers’ company administrators to install Falcon Prevent on their employees’ home systems. We believe both of these initiatives have been well received by our customers
Conclusion
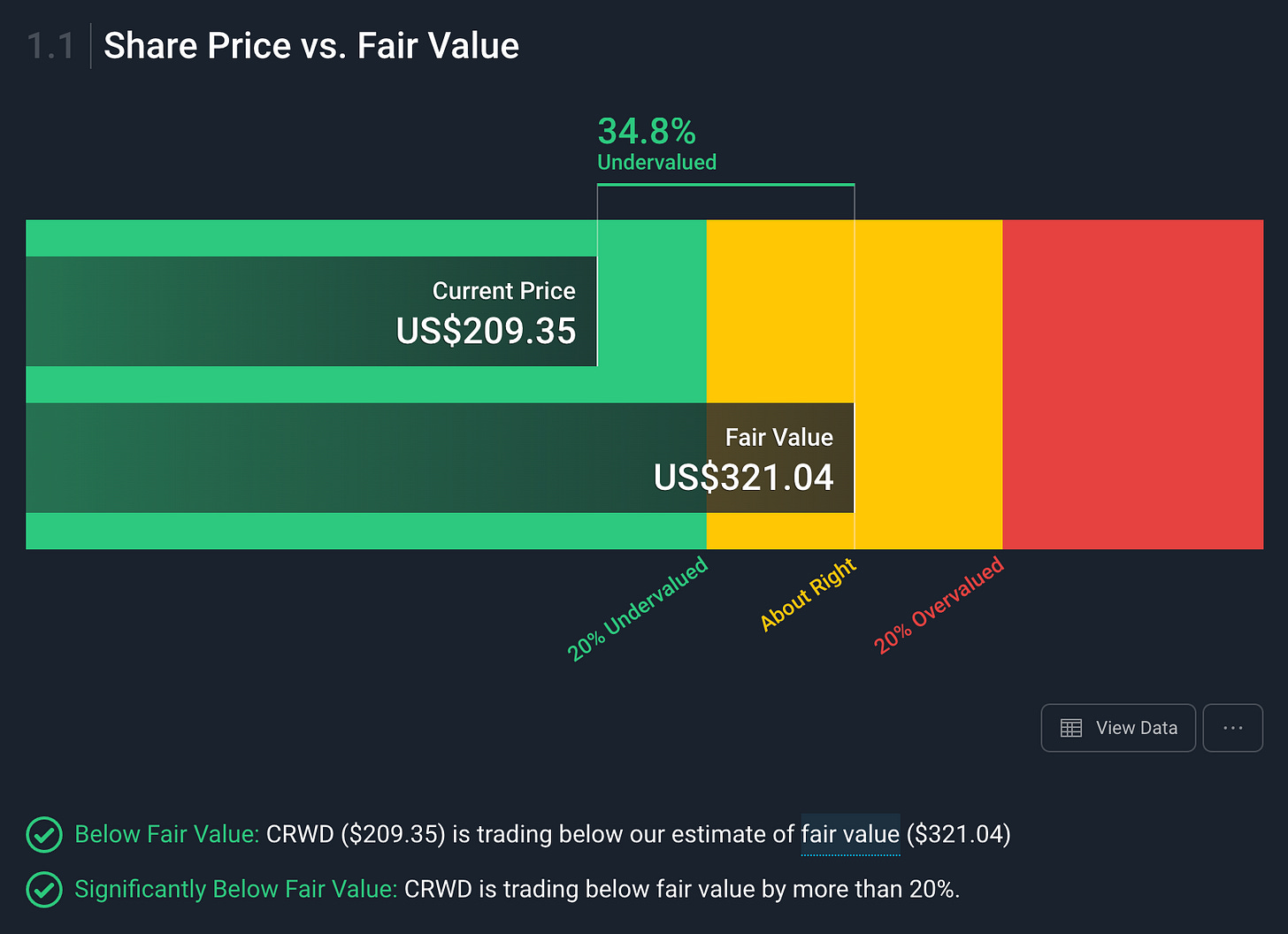
I think Crowdstrike is absolutely great company, with a killer valuation. Killer as in, it’ll kill me 😅 I don’t really do valuations unless I feel like I have to, but Simplywall.st has them as undervalued:
Thank you so much for reading this :) If you liked this do subscribe for free to the newsletter, I plan on posting regular deep-dives into companies.
Feel free to comment and let me know if I got something wrong, or your own thesis, for I seek the truth:
“If someone is able to show me that what I think or do is not right, I will happily change, for I seek the truth, by which no one was ever truly harmed. It is the person who continues in his self-deception and ignorance who is harmed.” - Marcus Aurelius
